My previous post Remote Desktop + SSH/Putty covered one approach for accessing your home PC via a strong security, strong encryption SSH tunnel. SSL-Explorer from 3SP also looks like a very simple way to remotely access your PC. I first heard of this project when it was mentioned on Steve Gibson's 'Security Now!' podcast (episode 15). There is also a review on Tom's Networking: A DIY SSL VPN with SSL-Explorer, and part 2. After reading the review I was left with a few questions, and sensing some material for a blog article. I'm about to install SSL-Explorer on a spare PC: and try answering some of my questions.
SSL-Explorer is an web-based SSL VPN server. A VPN exists for a secure external access to resources you have one your network. Perfect for 'roadwarrior' staff to access internal files and desktops from external sites, such as a hotel room, or home. SSL-Explorer provides this though a web-browser interface.
Once installed you get a web-based admin to administer the application - create users, set-up permissions, and configure the resources that will be made available to the users. A user connects via a browser, after logging-in they are presented a simple screen displaying the resources they have access to. Users can access the web securely, view Remote Desktops, and transfer files all via SSL-Explorer.
 SSL-Explorer's User Console displaying the 'Applications' available to the user.
SSL-Explorer's User Console displaying the 'Applications' available to the user.
The fresh install allows me to create: Web Forwards, Network Places, Applications, and SSL Tunnels. My first question was: how exactly do you make applications available via a web browser? The Tom's Hardware article goes through the steps of creating a VNC connection back to a server behind the firewall in the section "Checking out Remote Desktop". More questions:
- Where is this VNC executing?
- If it is executing on the client:
- How did it get there?
- How can it connect to the VNC behind the firewall?
Trying this out on my own set-up: in the admininstration I first set-up the VNC application short cut. I'm presented will a lot of options for the short cut:
Logging into the website as a 'user' I now have an option to launch VNC. Launching the app reveals an extra component to the SSL-Explorer application: the SSL-Explorer Agent. The first time I attempt to launch the VNC application from the web console - I'm prompted to install a signed java applet. This launches the SSL-Explorer Agent on my client.
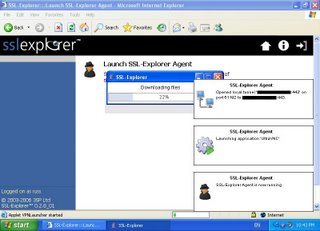
The SSL-Explorer Agent has:
- copied the application down to my PC (a search finds the application in %USERPROFILE%\.sslexplorer\applications),
- created a tunnel port on the client PC,
- and launched the VNC application with the command line options to connect to the tunnel port.
So the application sharing is conceptually very similar to using SSH tunnels to connect to a server behind a firewall. VNC is connecting a tunnel port on the local machine created by SSL-Explorer Agent. The agent is transferring this data to the SSL-Explorer application via SSL - which then transfers the data to and from the VNC server. SSL-Explorer is wrapping this up in a nice web interface. Not all applications are suitable to be shared this way. To work, an application needs to:
- Be the client in a TCP client/server environment, i.e. Remote Desktop, VNC, Putty.
- Allow the server address and port to be 'fed in' to the app, either via a command line argument, or config file. This is how the SSL-Explorer Agent tells the client to connect to the local tunnel port. The multitude of options available when creating the VNC shortcut is used to create a VNC parameter file on the client machine. This rules out MSN Messenger and Skype as they are 'hardcoded' with their server address and port.
Notably all the applications that come out of the box prompt the user for a password when a password is not present in the command line or config. Presumably this is preferable to leaving a password on the client machine.
Well that's answered the initial questions I had of SSL-Explorer, and has given me some more questions for my next blog post. Maybe try my hand at creating my own application extension? I've had a quick look around for a minimal Jabber client which meets all the criteria, may play a bit more with that. Also thinking of using a snooping proxy to see what is actually going over the HTTPS wire (Charles Proxy is capable of this). If someone were given an account without any tunnels setup - could you falsify the server traffic to have the agent create a tunnel?