Charles Proxy
|
|
The article you are reading has moved! It is now available at: http://blog.tinisles.com/2006/10/charles-proxy/ |
Checking out Charles Web Debugging Proxy while I'm having a bit of a look under of the hood of SSL-Explorer. Snooping on an a SSL session works straight out of the box. Must be using a 'man-in-the-middle' method to sit between me an the SSL website.
Yet, when I access https://www.amazon.com via Charles Proxy I get a warning about the certificate. Viewing the certificate 'certification path' shows that the content coming from the proxy has been encrypted with a certificate signed by 'Charles CA Certificate'.
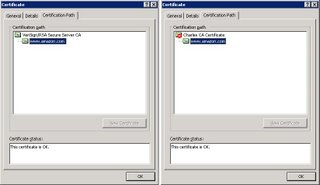
I know SSL does protect itself against a man-in-the-middle attack - but I don't know exactly how this works. There's an SSL certificate on the server that's been signed by a 'certificate authority (CA)' - and your browser contains public keys of the trusted CAs (IE: Tools -> Options -> Content -> Certificates -> Trusted Root Certification Authorities, Firefox: Tools -> Options -> Advanced -> Security -> View Certificates -> Authorities). How do these pieces fit together to protect against this attack?
More material for a blog post - stay tuned for the update. In the mean time I'll be translating this:
-
SSL 3.0 includes support for ephemerally-keyed
Diffie-Hellman key-exchange. Since Diffie-Hellman
is the only public key algorithm known which can
effciently provide perfect forward secrecy, this is
an excellent addition to SSL. In a SSL 3.0 Diffie-
Hellman key-exchange, the server specifes its Diffie-
Hellman exponent as well as the prime modulus and
generator. To avoid server-generated trapdoors, the
client should be careful to check that the modulus
and generator are from a fixed public list of safe
values. The well-known man-in-the-middle attack is
prevented in SSL 3.0 by requiring the server's Diffie-
Hellman exponential to be authenticated.
(Bruce Schneier - Analysis of the SSL 3.0 Protocol)
Labels: networking, web dev

Hi, I'm the author of Charles. I thought I could shed some light on this one!
SSL protects from the man-in-the-middle attack exactly as you've seen it. In order to observe the SSL communication (as Charles does so you can observe it too), Charles has to create a new SSL session with your browser and sign it using its own CA certificate. Unless your CA certificate is trusted by the browser you see a warning as shown, which is how your browser enables you to detect that something is wrong - in this case a man-in-the-middle. Because you're expecting (hopefully!) the man-in-the-middle you can allow it.
I hope that helps!
Kind regards,
Karl
Posted by Anonymous |
6:01 am
Anonymous |
6:01 am
Hi Karl, thanks for the detailed comment! I eventually did follow up this 'question' post with a look at the inner workings of SSL : SSL + Man-in-the-Middle
Posted by Russ |
9:26 am
Russ |
9:26 am
Amazing blog! I really like the way you explained such information about this post with us. And blog is really helpful for us this website
allsoftwarepro.com
reviversoft-security-reviver-crack
virtual-safe-professional-crack
charles-proxy-crack
corel-windvd-pro-crack
abelssoft-filefusion-crack
Posted by Allsoftwarepro |
6:57 pm
Allsoftwarepro |
6:57 pm
I like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
Very interesting blog.
tomabo-mp4-downloader Crack
pandora-radio Crack
mobaxterm Crack
joyoshare-heic-converter Crack
archicad Crack
microsoft-office-professional Crack
pdf-shaper-professional Crack
abelssoft-filefusion Crack
Posted by wasem khani |
4:03 am
wasem khani |
4:03 am
Just admiring your work and wondering how you managed this blog so well. It’s so remarkable that I can't afford to not go through this valuable information whenever I surf the internet! android emulators
charles-web-debugging-proxy-crack
autodesk-alias-surface-crack
dr-fone-crack
iobit-uninstaller-pro-crack
utorrent-pro-crack
eximioussoft-logo-designer-pro-crack
screenfloat-crack
tuneskit-audio-converter-crack
Posted by Crackglobal |
2:34 am
Crackglobal |
2:34 am